题目给了个图片
以及一句提示 “斯蒂xx会帮助你”
直接就能想到 ste 开头的那几个工具,但是我比赛时候电脑什么ste开头的工具都没装,只能回来做了。
└─$ exiftool x.jpeg
ExifTool Version Number : 13.00
File Name : x.jpeg
Directory : .
File Size : 89 kB
File Modification Date/Time : 2024:04:25 07:44:30-04:00
File Access Date/Time : 2025:08:23 03:54:40-04:00
File Inode Change Date/Time : 2025:08:22 03:10:33-04:00
File Permissions : -rw-rw-r--
File Type : JPEG
File Type Extension : jpg
MIME Type : image/jpeg
JFIF Version : 1.01
Resolution Unit : inches
X Resolution : 72
Y Resolution : 72
Exif Byte Order : Big-endian (Motorola, MM)
XP Comment : jzxcvb123
Padding : (Binary data 268 bytes, use -b option to extract)
Image Width : 422
Image Height : 750
Encoding Process : Baseline DCT, Huffman coding
Bits Per Sample : 8
Color Components : 3
Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)
Image Size : 422x750
Megapixels : 0.317
其中XP Comment 部分给了个 XP Comment
010打开,结尾有填充数据
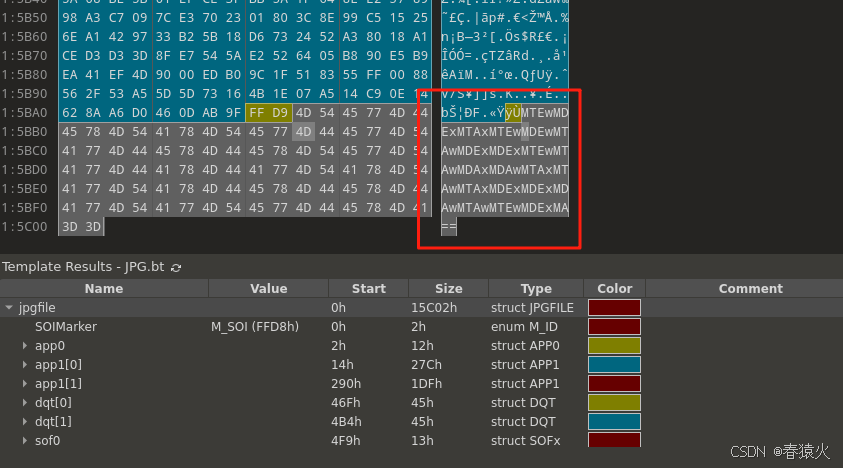
解出后为一串二进制
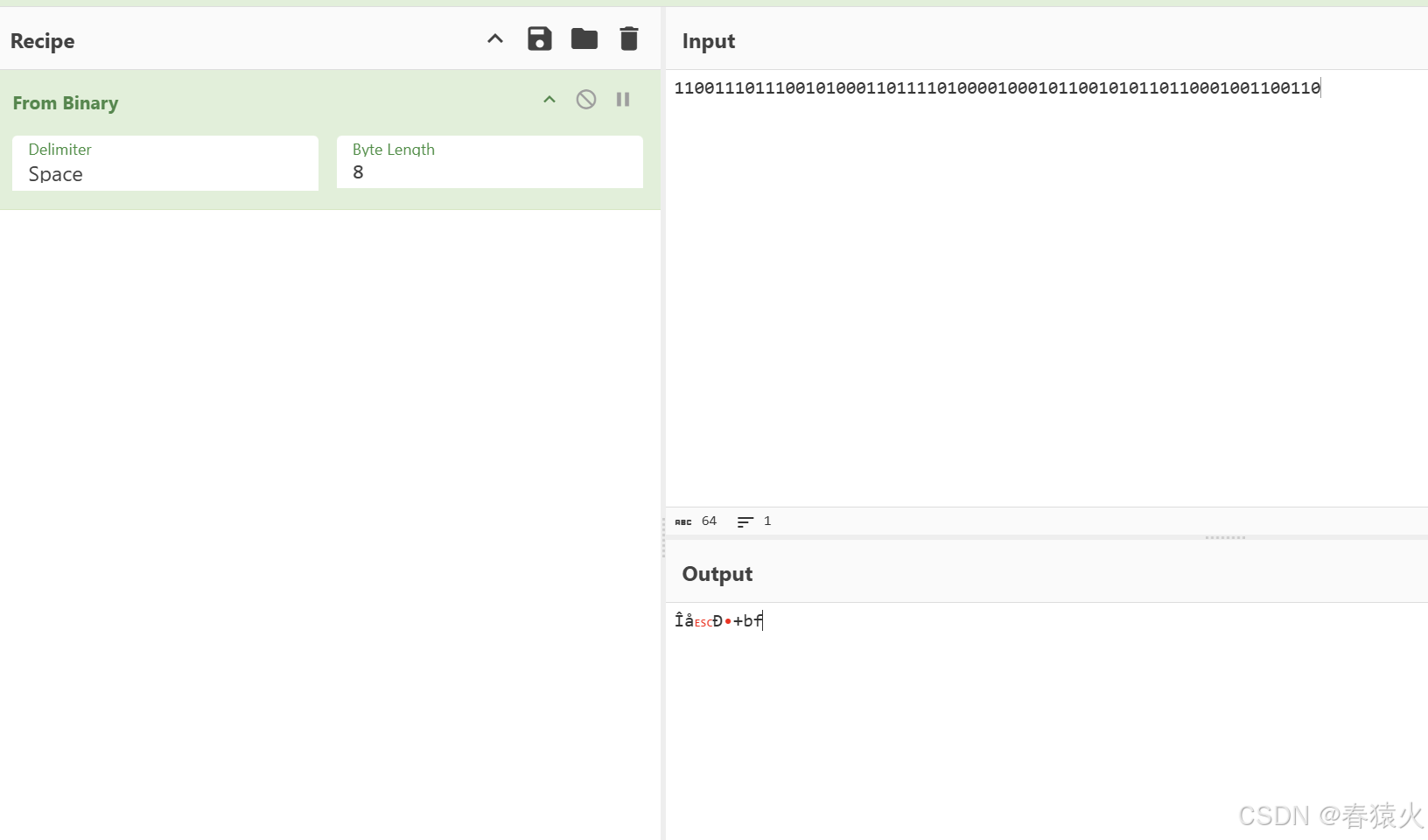
└─$ echo -en 'MTEwMDExMTAxMTEwMDEwMTAwMDExMDExMTEwMTAwMDAxMDAwMTAxMTAwMTAxMDExMDExMDAwMTAwMTEwMDExMA=='|base64 -d
1100111011100101000110111101000010001011001010110110001001100110
这里取8位转bin处理,无法得到有效信息
依照题目提示尝试工具
这里steghide要密码
└─$ steghide info x.jpeg
"x.jpeg":format: jpegcapacity: 5.3 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
steghide: could not extract any data with that passphrase!
用刚才 XP Comment 的尝试提交
└─$ steghide info x.jpeg -p jzxcvb123
"x.jpeg":format: jpegcapacity: 5.3 KBembedded file "test.zip":size: 2.5 KBencrypted: rijndael-128, cbccompressed: yes
里面藏了个压缩包,提取
└─$ steghide extract -sf x.jpeg -p jzxcvb123
wrote extracted data to "test.zip"
压缩包放了个flag.txt和一个elf
└─$ zipinfo test.zip
Archive: test.zip
Zip file size: 2518 bytes, number of entries: 2
-rw-a-- 2.0 fat 20 BX defN 24-Apr-25 14:46 flag.txt
-rw-a-- 2.0 fat 6120 BX defN 24-Apr-25 14:29 test
2 files, 6140 bytes uncompressed, 2224 bytes compressed: 63.8%
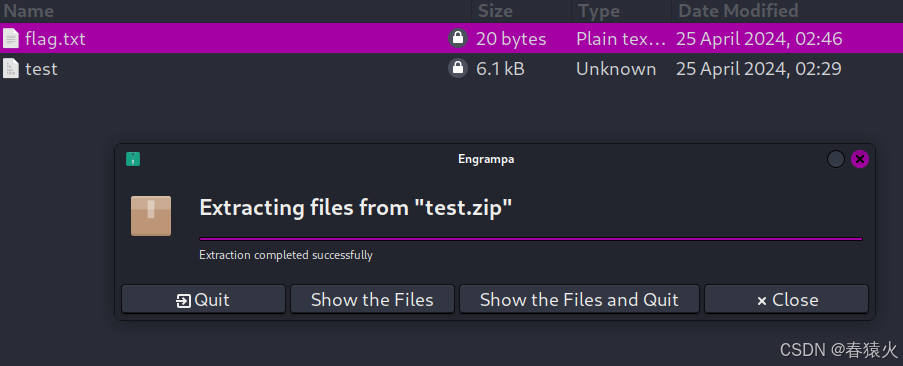
解压提示有密码
└─$ unzip test.zip -d test
Archive: test.zip
[test.zip] flag.txt password:
导hash跑不出密码,考虑伪加密
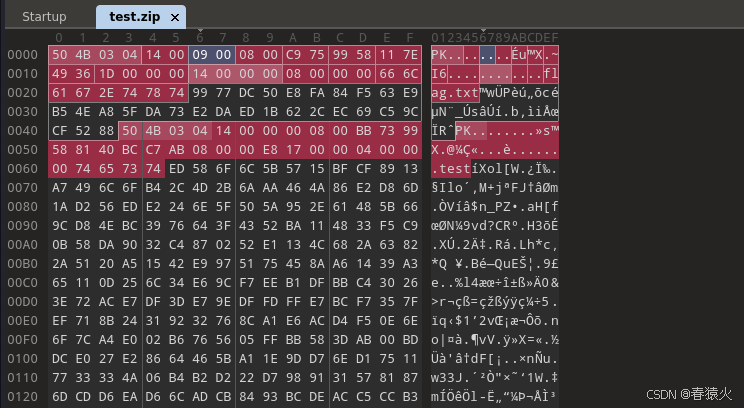
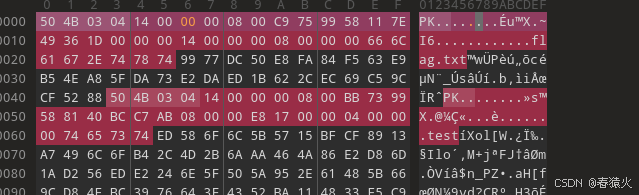
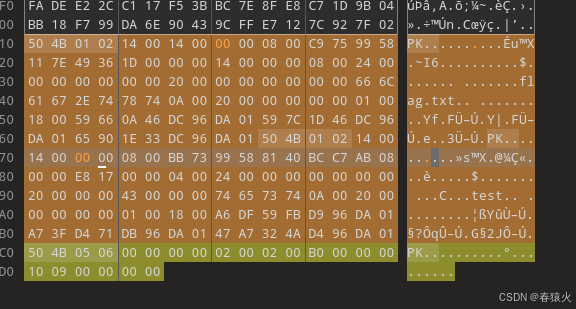
test可以正常解压是个伪加密,flag.txt不行
└─$ unzip test.zip -d test
Archive: test.zipinflating: test/flag.txt error: invalid compressed data to inflateinflating: test/test
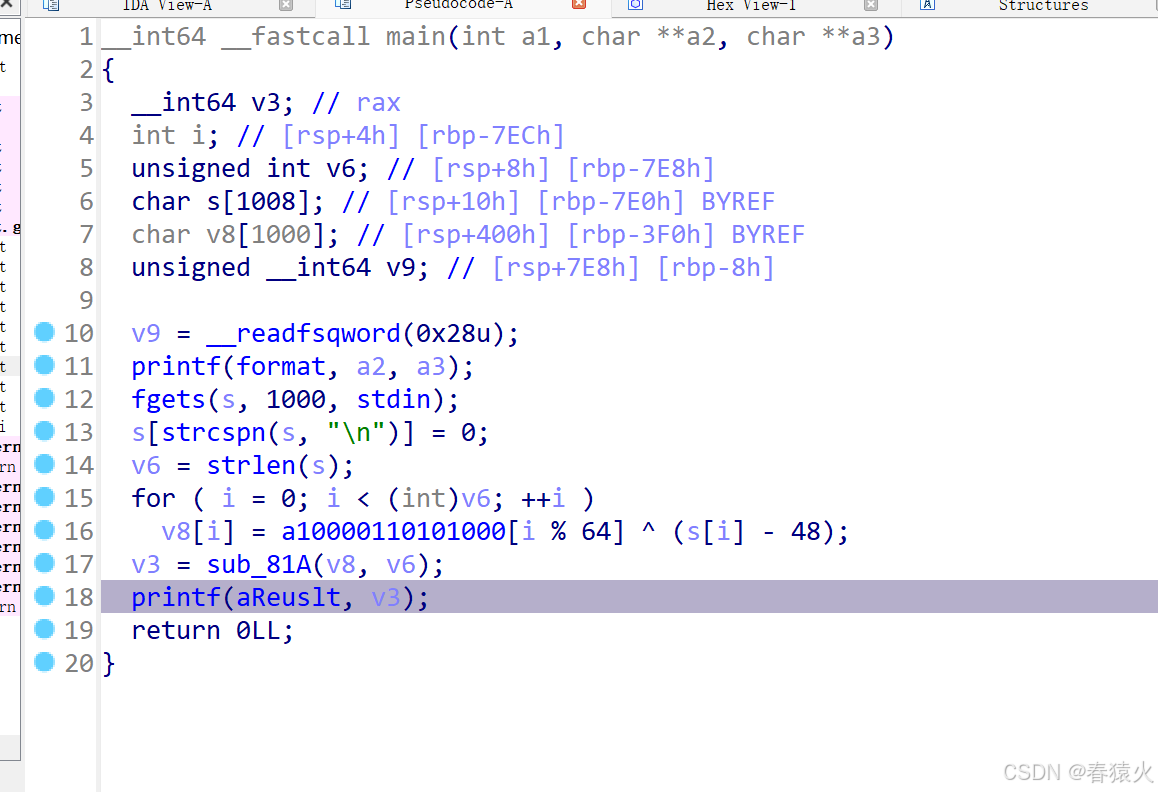
这边是两个字符串做异或
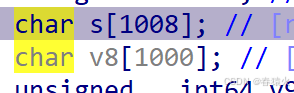
sub_81A 则是+48把0和1转回ascii
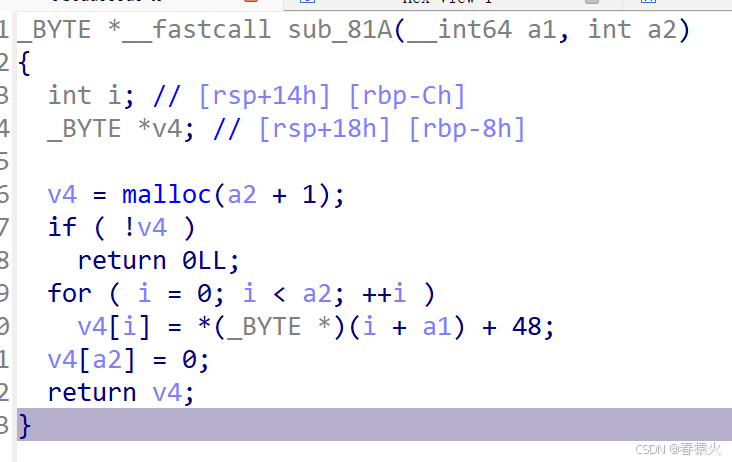
所以简单写个还原即可
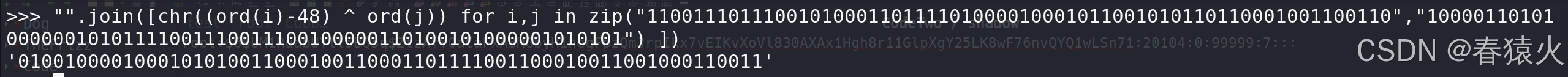
>>> "".join([chr((ord(i)-48) ^ ord(j)) for i,j in zip("1100111011100101000110111101000010001011001010110110001001100110","1000011010100000010101111001110011100100000110100101000001010101") ])
'0100100001000101010011000100110001101111001100010011001000110011'
加+48得到原始输入内容
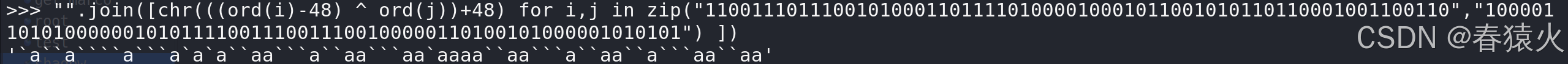
>>> "".join([chr(((ord(i)-48) ^ ord(j))+48) for i,j in zip("1100111011100101000110111101000010001011001010110110001001100110","1000011010100000010101111001110011100100000110100101000001010101") ])
'`a``a````a```a`a`a``aa```a``aa```aa`aaaa``aa```a``aa``a```aa``aa'
验证下
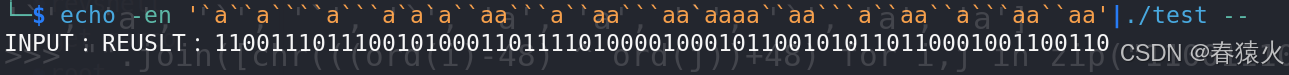
再中间+48前的那个数字部分,bin转一下会得到一串ascii
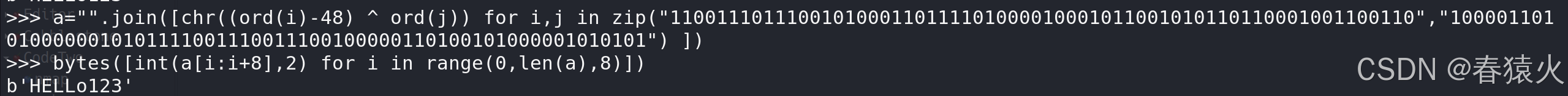
>>> bytes([int(a[i:i+8],2) for i in range(0,len(a),8)])
>b'HELLo123'
拿去解压flag.txt
得到flag
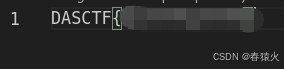
![[系统架构设计师]大数据架构设计理论与实践(十九)](http://pic.xiahunao.cn/[系统架构设计师]大数据架构设计理论与实践(十九))

)



(获取方式看绑定的资源))












