NAT 实验
一.实验拓扑图
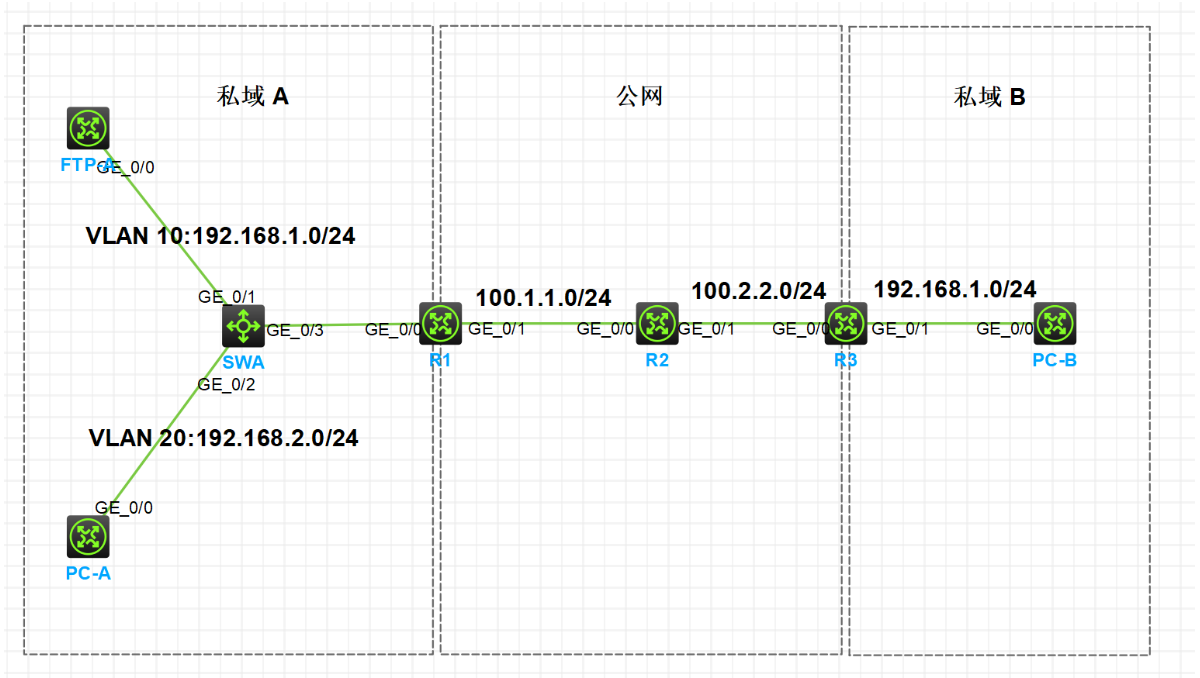
实验目的
1.按照图示配置 IP 地址
2.私网 A 通过 R1 接入到互联网,私网 B 通过 R3 接入到互联网
3.私网 A 内部存在 Vlan10 和 Vlan20,通过 R1 上单臂路由访问外部网络
4.私网 A 通过 NAPT 使 Vlan10 和 Vlan20 都能够使用 R1 的公网地址访问互联网
5.私网 B 通过在 R3 上配置 EASY IP 访问互联网
- 私网 A 配置 NAT SERVER 把 FTPA 的 FTP 服务发布到公网,使 PCB 可以访问
二.实验步骤
1.按照图示配置 IP 地址(略)
2.私网 A 内部存在 Vlan10 和 Vlan20,通过 R1 上单臂路由访问外部网络
在SWA上配置vlan
[SWA]vlan 10
[SWA-vlan10]port g1/0/1
[SWA-vlan10]vlan 20
[SWA-vlan20]port g1/0/2
[SWA-vlan20]int g1/0/3
[SWA-GigabitEthernet1/0/3]port link-type trunk
[SWA-GigabitEthernet1/0/3]port trunk permit vlan 10 20
[SWA-GigabitEthernet1/0/3]quit
[SWA]
R1上配置单臂路由
[R1]int g0/0.1
[R1-GigabitEthernet0/0.1]%Jul 14 20:14:04:407 2025 R1 IFNET/3/PHY_UPDOWN: Physical state on the interface GigabitEthernet0/0.1 changed to up.
%Jul 14 20:14:04:408 2025 R1 IFNET/5/LINK_UPDOWN: Line protocol state on the interface GigabitEthernet0/0.1 changed to up.[R1-GigabitEthernet0/0.1]vlan-type dot1q vid 10
[R1-GigabitEthernet0/0.1]%Jul 14 20:14:35:506 2025 R1 IFNET/3/PHY_UPDOWN: Physical state on the interface GigabitEthernet0/0.1 changed to down.
%Jul 14 20:14:35:507 2025 R1 IFNET/5/LINK_UPDOWN: Line protocol state on the interface GigabitEthernet0/0.1 changed to down.
%Jul 14 20:14:35:507 2025 R1 IFNET/3/PHY_UPDOWN: Physical state on the interface GigabitEthernet0/0.1 changed to up.
%Jul 14 20:14:35:508 2025 R1 IFNET/5/LINK_UPDOWN: Line protocol state on the interface GigabitEthernet0/0.1 changed to up.[R1-GigabitEthernet0/0.1]ip address 192.168.1.254 24
[R1-GigabitEthernet0/0.1]int g0/0.2
[R1-GigabitEthernet0/0.2]%Jul 14 20:15:01:367 2025 R1 IFNET/3/PHY_UPDOWN: Physical state on the interface GigabitEthernet0/0.2 changed to up.
%Jul 14 20:15:01:368 2025 R1 IFNET/5/LINK_UPDOWN: Line protocol state on the interface GigabitEthernet0/0.2 changed to up.[R1-GigabitEthernet0/0.2]vlan-type dot1q vid 20
[R1-GigabitEthernet0/0.2]%Jul 14 20:15:18:631 2025 R1 IFNET/3/PHY_UPDOWN: Physical state on the interface GigabitEthernet0/0.2 changed to down.
%Jul 14 20:15:18:632 2025 R1 IFNET/5/LINK_UPDOWN: Line protocol state on the interface GigabitEthernet0/0.2 changed to down.
%Jul 14 20:15:18:632 2025 R1 IFNET/3/PHY_UPDOWN: Physical state on the interface GigabitEthernet0/0.2 changed to up.
%Jul 14 20:15:18:632 2025 R1 IFNET/5/LINK_UPDOWN: Line protocol state on the interface GigabitEthernet0/0.2 changed to up.[R1-GigabitEthernet0/0.2]ip address 192.168.2.254 24
[R1-GigabitEthernet0/0.2]
[R1-GigabitEthernet0/0.2]quit
[R1]dis ip int b
*down: administratively down
(s): spoofing (l): loopback
Interface Physical Protocol IP address/Mask VPN instance Description
GE0/0 up up -- -- --
GE0/0.1 up up 192.168.1.254/24 -- --
GE0/0.2 up up 192.168.2.254/24 -- --
GE0/1 up up 100.1.1.1/24 -- --
GE0/2 down down -- -- --
GE5/0 down down -- -- --
GE5/1 down down -- -- --
GE6/0 down down -- -- --
GE6/1 down down -- -- --
Ser1/0 down down -- -- --
Ser2/0 down down -- -- --
Ser3/0 down down -- -- --
Ser4/0 down down -- -- --
[R2]dis ip int b
*down: administratively down
(s): spoofing (l): loopback
Interface Physical Protocol IP address/Mask VPN instance Description
GE0/0 up up 100.1.1.2/24 -- --
GE0/1 up up 100.2.2.2/24 -- --
GE0/2 down down -- -- --
GE5/0 down down -- -- --
GE5/1 down down -- -- --
GE6/0 down down -- -- --
GE6/1 down down -- -- --
Ser1/0 down down -- -- --
Ser2/0 down down -- -- --
Ser3/0 down down -- -- --
Ser4/0 down down -- -- --
[R3]dis ip int b
*down: administratively down
(s): spoofing (l): loopback
Interface Physical Protocol IP address/Mask VPN instance Description
GE0/0 up up 100.2.2.3/24 -- --
GE0/1 up up 192.168.1.3/24 -- --
GE0/2 down down -- -- --
GE5/0 down down -- -- --
GE5/1 down down -- -- --
GE6/0 down down -- -- --
GE6/1 down down -- -- --
Ser1/0 down down -- -- --
Ser2/0 down down -- -- --
Ser3/0 down down -- -- --
Ser4/0 down down -- -- --
[FTP-A]dis ip int b
*down: administratively down
(s): spoofing (l): loopback
Interface Physical Protocol IP address/Mask VPN instance Description
GE0/0 up up 192.168.1.1/24 -- --
GE0/1 down down -- -- --
GE0/2 down down -- -- --
GE5/0 down down -- -- --
GE5/1 down down -- -- --
GE6/0 down down -- -- --
GE6/1 down down -- -- --
Ser1/0 down down -- -- --
Ser2/0 down down -- -- --
Ser3/0 down down -- -- --
Ser4/0 down down -- -- --
[PC-A]dis ip int b
*down: administratively down
(s): spoofing (l): loopback
Interface Physical Protocol IP address/Mask VPN instance Description
GE0/0 up up 192.168.2.1/24 -- --
GE0/1 down down -- -- --
GE0/2 down down -- -- --
GE5/0 down down -- -- --
GE5/1 down down -- -- --
GE6/0 down down -- -- --
GE6/1 down down -- -- --
Ser1/0 down down -- -- --
Ser2/0 down down -- -- --
Ser3/0 down down -- -- --
Ser4/0 down down -- -- --
[PC-B]dis ip int b
*down: administratively down
(s): spoofing (l): loopback
Interface Physical Protocol IP address/Mask VPN instance Description
GE0/0 up up 192.168.1.4/24 -- --
GE0/1 down down -- -- --
GE0/2 down down -- -- --
GE5/0 down down -- -- --
GE5/1 down down -- -- --
GE6/0 down down -- -- --
GE6/1 down down -- -- --
Ser1/0 down down -- -- --
Ser2/0 down down -- -- --
Ser3/0 down down -- -- --
Ser4/0 down down -- -- --
测试PC-A和FTP-A是否能和R1互通
[PC-A]ping 192.168.2.254
Ping 192.168.2.254 (192.168.2.254): 56 data bytes, press CTRL+C to break
56 bytes from 192.168.2.254: icmp_seq=0 ttl=255 time=5.224 ms
56 bytes from 192.168.2.254: icmp_seq=1 ttl=255 time=9.641 ms
56 bytes from 192.168.2.254: icmp_seq=2 ttl=255 time=2.589 ms
56 bytes from 192.168.2.254: icmp_seq=3 ttl=255 time=2.158 ms
56 bytes from 192.168.2.254: icmp_seq=4 ttl=255 time=2.086 ms--- Ping statistics for 192.168.2.254 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 2.086/4.340/9.641/2.891 ms
[PC-A]%Jul 14 20:29:13:266 2025 PC-A PING/6/PING_STATISTICS: Ping statistics for 192.168.2.254: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 2.086/4.340/9.641/2.891 ms.
[FTP-A]ping 192.168.1.254
Ping 192.168.1.254 (192.168.1.254): 56 data bytes, press CTRL+C to break
56 bytes from 192.168.1.254: icmp_seq=0 ttl=255 time=2.710 ms
56 bytes from 192.168.1.254: icmp_seq=1 ttl=255 time=4.101 ms
56 bytes from 192.168.1.254: icmp_seq=2 ttl=255 time=2.409 ms
56 bytes from 192.168.1.254: icmp_seq=3 ttl=255 time=0.970 ms
56 bytes from 192.168.1.254: icmp_seq=4 ttl=255 time=3.003 ms--- Ping statistics for 192.168.1.254 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 0.970/2.639/4.101/1.011 ms
[FTP-A]%Jul 14 20:29:01:192 2025 FTP-A PING/6/PING_STATISTICS: Ping statistics for 192.168.1.254: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 0.970/2.639/4.101/1.011 ms.
[FTP-A]ping 192.168.2.1
Ping 192.168.2.1 (192.168.2.1): 56 data bytes, press CTRL+C to break
Request time out
Request time out
Request time out
Request time out
Request time out--- Ping statistics for 192.168.2.1 ---
5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss
[FTP-A]%Jul 14 20:45:58:759 2025 FTP-A PING/6/PING_STATISTICS: Ping statistics for 192.168.2.1: 5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss.
但是我们会发现FTP-A ping PC-A是不通的,因为我们这两台设备上缺少网关
[FTP-A]ip route-static 0.0.0.0 0 192.168.1.254
[FTP-A]dis th
#sysname FTP-A
#system-working-mode standardxbar load-singlepassword-recovery enablelpu-type f-series
#scheduler logfile size 16
#ip route-static 0.0.0.0 0 192.168.1.254
#domain default enable system
#
return
[PC-A]ip route-static 0.0.0.0 0 192.168.2.254
[PC-A]dis th
#sysname PC-A
#system-working-mode standardxbar load-singlepassword-recovery enablelpu-type f-series
#scheduler logfile size 16
#ip route-static 0.0.0.0 0 192.168.2.254
#domain default enable system
#
return
测试效果
[FTP-A]ping 192.168.2.1
Ping 192.168.2.1 (192.168.2.1): 56 data bytes, press CTRL+C to break
56 bytes from 192.168.2.1: icmp_seq=0 ttl=254 time=3.135 ms
56 bytes from 192.168.2.1: icmp_seq=1 ttl=254 time=4.829 ms
56 bytes from 192.168.2.1: icmp_seq=2 ttl=254 time=5.019 ms
56 bytes from 192.168.2.1: icmp_seq=3 ttl=254 time=5.016 ms
56 bytes from 192.168.2.1: icmp_seq=4 ttl=254 time=5.156 ms--- Ping statistics for 192.168.2.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 3.135/4.631/5.156/0.755 ms
[FTP-A]%Jul 14 20:57:29:430 2025 FTP-A PING/6/PING_STATISTICS: Ping statistics for 192.168.2.1: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 3.135/4.631/5.156/0.755 ms.
[PC-A]ping 192.168.1.1
Ping 192.168.1.1 (192.168.1.1): 56 data bytes, press CTRL+C to break
56 bytes from 192.168.1.1: icmp_seq=0 ttl=254 time=4.138 ms
56 bytes from 192.168.1.1: icmp_seq=1 ttl=254 time=5.219 ms
56 bytes from 192.168.1.1: icmp_seq=2 ttl=254 time=4.126 ms
56 bytes from 192.168.1.1: icmp_seq=3 ttl=254 time=4.564 ms
56 bytes from 192.168.1.1: icmp_seq=4 ttl=254 time=4.192 ms--- Ping statistics for 192.168.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 4.126/4.448/5.219/0.418 ms
[PC-A]%Jul 14 20:58:42:261 2025 PC-A PING/6/PING_STATISTICS: Ping statistics for 192.168.1.1: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 4.126/4.448/5.219/0.418 ms.
现在,私域 A已经全部互通
3.R1 和 R3 上配置默认路由指向公网
[R1]ip route-static 0.0.0.0 0 100.1.1.2
[R3]ip route-static 0.0.0.0 0 100.2.2.2
再次查看效果
[R1]ping 100.1.1.2
Ping 100.1.1.2 (100.1.1.2): 56 data bytes, press CTRL+C to break
56 bytes from 100.1.1.2: icmp_seq=0 ttl=255 time=1.399 ms
56 bytes from 100.1.1.2: icmp_seq=1 ttl=255 time=1.215 ms
56 bytes from 100.1.1.2: icmp_seq=2 ttl=255 time=1.958 ms
56 bytes from 100.1.1.2: icmp_seq=3 ttl=255 time=1.285 ms
56 bytes from 100.1.1.2: icmp_seq=4 ttl=255 time=1.145 ms--- Ping statistics for 100.1.1.2 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 1.145/1.400/1.958/0.291 ms
[R1]%Jul 14 21:09:56:772 2025 R1 PING/6/PING_STATISTICS: Ping statistics for 100.1.1.2: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 1.145/1.400/1.958/0.291 ms.[R1]
[R1]ping 100.2.2.3
Ping 100.2.2.3 (100.2.2.3): 56 data bytes, press CTRL+C to break
56 bytes from 100.2.2.3: icmp_seq=0 ttl=254 time=2.265 ms
56 bytes from 100.2.2.3: icmp_seq=1 ttl=254 time=3.000 ms
56 bytes from 100.2.2.3: icmp_seq=2 ttl=254 time=1.827 ms
56 bytes from 100.2.2.3: icmp_seq=3 ttl=254 time=1.757 ms
56 bytes from 100.2.2.3: icmp_seq=4 ttl=254 time=2.346 ms--- Ping statistics for 100.2.2.3 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 1.757/2.239/3.000/0.446 ms
[R1]%Jul 14 21:13:23:081 2025 R1 PING/6/PING_STATISTICS: Ping statistics for 100.2.2.3: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 1.757/2.239/3.000/0.446 ms.R1和R3能通
[FTP-A]ping 100.1.1.1
Ping 100.1.1.1 (100.1.1.1): 56 data bytes, press CTRL+C to break
56 bytes from 100.1.1.1: icmp_seq=0 ttl=255 time=1.228 ms
56 bytes from 100.1.1.1: icmp_seq=1 ttl=255 time=2.460 ms
56 bytes from 100.1.1.1: icmp_seq=2 ttl=255 time=3.195 ms
56 bytes from 100.1.1.1: icmp_seq=3 ttl=255 time=2.988 ms
56 bytes from 100.1.1.1: icmp_seq=4 ttl=255 time=3.005 ms--- Ping statistics for 100.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 1.228/2.575/3.195/0.717 ms
[FTP-A]%Jul 14 21:05:06:410 2025 FTP-A PING/6/PING_STATISTICS: Ping statistics for 100.1.1.1: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 1.228/2.575/3.195/0.717 ms.[FTP-A]
[FTP-A]
[FTP-A]ping 100.1.1.2
Ping 100.1.1.2 (100.1.1.2): 56 data bytes, press CTRL+C to break
Request time out
Request time out
Request time out
Request time out
Request time out--- Ping statistics for 100.1.1.2 ---
5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss
[FTP-A]%Jul 14 21:11:35:248 2025 FTP-A PING/6/PING_STATISTICS: Ping statistics for 100.1.1.2: 5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss.
FTP-A能通到R1不能通到R2
[PC-B]ping 192.168.1.3
Ping 192.168.1.3 (192.168.1.3): 56 data bytes, press CTRL+C to break
56 bytes from 192.168.1.3: icmp_seq=0 ttl=255 time=1.007 ms
56 bytes from 192.168.1.3: icmp_seq=1 ttl=255 time=1.457 ms
56 bytes from 192.168.1.3: icmp_seq=2 ttl=255 time=1.316 ms
56 bytes from 192.168.1.3: icmp_seq=3 ttl=255 time=1.588 ms
56 bytes from 192.168.1.3: icmp_seq=4 ttl=255 time=1.359 ms--- Ping statistics for 192.168.1.3 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 1.007/1.345/1.588/0.193 ms
[PC-B]%Jul 14 21:12:03:771 2025 PC-B PING/6/PING_STATISTICS: Ping statistics for 192.168.1.3: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 1.007/1.345/1.588/0.193 ms.[PC-B]
[PC-B]ping 100.2.2.2
Ping 100.2.2.2 (100.2.2.2): 56 data bytes, press CTRL+C to break
Request time out
Request time out
Request time out--- Ping statistics for 100.2.2.2 ---
4 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss
[PC-B]%Jul 14 21:15:55:413 2025 PC-B PING/6/PING_STATISTICS: Ping statistics for 100.2.2.2: 4 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss.
PC-B能通到R3不能通到R2
[R1]ping 192.168.1.4
Ping 192.168.1.4 (192.168.1.4): 56 data bytes, press CTRL+C to break
Request time out
Request time out
Request time out
Request time out
Request time out--- Ping statistics for 192.168.1.4 ---
5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss
%Jul 14 21:19:45:794 2025 R1 PING/6/PING_STATISTICS: Ping statistics for 192.168.1.4: 5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss.
[R1]
R1不能通到PC-B,那么证明私域 A 内部能互通,私域 B 内部能互通,公网内部也能互通,但这三个区域不能彼此互通
4.私网 A 通过 NAPT 使 Vlan10 和 Vlan20 都能够使用 R1 的公网地址访问互联网
分析:根据需求得知,ACL 需要配置允许 192.168.1.0/24 和 192.168.2.0/24 网段;私网 A 只有 1 个公网地址可用,意味着创建的 NAT 地址池起始和结束地址就都是 100.1.1.1
(1)R1 上创建基本 ACL,允许 192.168.1.0/24 和 192.168.2.0/24 网段
[R1]acl basic 2000
[R1-acl-ipv4-basic-2000]rule permit source 192.168.1.0 0.0.0.255
[R1-acl-ipv4-basic-2000]rule permit source 192.168.2.0 0.0.0.255
[R1-acl-ipv4-basic-2000]dis th
#
acl basic 2000rule 0 permit source 192.168.1.0 0.0.0.255rule 5 permit source 192.168.2.0 0.0.0.255
#
return
ACL是命中条件,命中之后再转给NAT
(2)R1 上创建 NAT 地址池,设置公网地址
[R1]nat address-group 1
[R1-address-group-1]address 100.1.1.1 100.1.1.1
[R1-address-group-1]dis th
#
nat address-group 1address 100.1.1.1 100.1.1.1
#
return
(3)在 R1 的公网接口上配置 NAPT
[R1]int g0/1
[R1-GigabitEthernet0/1]nat outbound 2000 address-group 1
(4)在 PCA 上 Ping R3 的公网地址,测试是否可以访问互联网
[FTP-A]ping 100.1.1.2
Ping 100.1.1.2 (100.1.1.2): 56 data bytes, press CTRL+C to break
56 bytes from 100.1.1.2: icmp_seq=0 ttl=254 time=5.735 ms
56 bytes from 100.1.1.2: icmp_seq=1 ttl=254 time=2.421 ms
56 bytes from 100.1.1.2: icmp_seq=2 ttl=254 time=3.432 ms
56 bytes from 100.1.1.2: icmp_seq=3 ttl=254 time=1.527 ms
56 bytes from 100.1.1.2: icmp_seq=4 ttl=254 time=1.910 ms--- Ping statistics for 100.1.1.2 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 1.527/3.005/5.735/1.507 ms
[FTP-A]%Jul 14 21:39:17:542 2025 FTP-A PING/6/PING_STATISTICS: Ping statistics for 100.1.1.2: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 1.527/3.005/5.735/1.507 ms.
5.私网 B 通过在 R3 上配置 EASY IP 访问互联网
分析:根据需求得知,ACL 需要配置允许 192.168.1.0/24 网段;使用 EASY IP,就无需配置 NAT 地址池,直接在公网接口上配置即可,EASY IP 会自动识别公网接口的 IP 地址
(1)R3 上创建基本 ACL,允许 192.168.1.0/24 网段
[R3]acl basic 2000
[R3-acl-ipv4-basic-2000]rule permit source 192.168.1.0 0.0.0.255
[R3-acl-ipv4-basic-2000]dis th
#
acl basic 2000rule 0 permit source 192.168.1.0 0.0.0.255
#
return
(2)在 R3 的公网接口上配置 EASY IP
[R3]int g0/0
[R3-GigabitEthernet0/0]nat outbound 2000
(3)先确保PC-B有网关(配置静态路由模拟网关)然后在 PCB 上 Ping R1 的公网地址,测试是否可以访问互联网
[PC-B]ip route-static 0.0.0.0 0 192.168.1.3
[PC-B]ping 100.2.2.2
Ping 100.2.2.2 (100.2.2.2): 56 data bytes, press CTRL+C to break
56 bytes from 100.2.2.2: icmp_seq=0 ttl=254 time=2.477 ms
56 bytes from 100.2.2.2: icmp_seq=1 ttl=254 time=1.338 ms
56 bytes from 100.2.2.2: icmp_seq=2 ttl=254 time=1.327 ms
56 bytes from 100.2.2.2: icmp_seq=3 ttl=254 time=2.726 ms
56 bytes from 100.2.2.2: icmp_seq=4 ttl=254 time=1.691 ms--- Ping statistics for 100.2.2.2 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 1.327/1.912/2.726/0.584 ms
[PC-B]%Jul 14 21:44:00:757 2025 PC-B PING/6/PING_STATISTICS: Ping statistics for 100.2.2.2: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 1.327/1.912/2.726/0.584 ms.
现在是私域 A 和私域 B 可以与公网互通,但是私域 A 和私域 B 彼此不能互通
6.私网 A 配置 NAT SERVER 把 FTPA 的 FTP 服务发布到公网,使 PCB 可以访问
根据需求得知,需要发布 FTPA 的 FTP 服务,也就是把 R1 的公网地址的 20 和 21 端口映射到 FTPA 的私网地址
(1)在FTP-A配置FTP服务:
[FTP-A]ftp server enable
[FTP-A]local-user stw class manage
New local user added.
[FTP-A-luser-manage-stw]password simple 123456.com
[FTP-A-luser-manage-stw]service-type ftp
[FTP-A-luser-manage-stw]authorization-attribute user-role level-15
[FTP-A-luser-manage-stw]quit
(2)在 R1 的公网接口上配置 NAT SERVER,映射端口 20 和 21
[R1]int g0/1
[R1-GigabitEthernet0/1]nat server protocol tcp global current-interface 20 21 in
side 192.168.1.1 20 21
[R1-GigabitEthernet0/1]dis th
#
interface GigabitEthernet0/1port link-mode routecombo enable copperip address 100.1.1.1 255.255.255.0nat outbound 2000 address-group 1nat server protocol tcp global current-interface 20 21 inside 192.168.1.1 20 21
#
return
(3)在 PCB 上测试是否能够通过 R1 的公网地址访问 FTPA 的 FTP 服务
<PC-B>ping 192.168.1.1
Ping 192.168.1.1 (192.168.1.1): 56 data bytes, press CTRL+C to break
Request time out
Request time out
Request time out
Request time out
Request time out--- Ping statistics for 192.168.1.1 ---
5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss
<PC-B>%Jul 14 22:00:30:541 2025 PC-B PING/6/PING_STATISTICS: Ping statistics for 192.168.1.1: 5 packet(s) transmitted, 0 packet(s) received, 100.0% packet loss.<PC-B>
<PC-B>ping 100.1.1.1
Ping 100.1.1.1 (100.1.1.1): 56 data bytes, press CTRL+C to break
56 bytes from 100.1.1.1: icmp_seq=0 ttl=253 time=3.378 ms
56 bytes from 100.1.1.1: icmp_seq=1 ttl=253 time=4.650 ms
56 bytes from 100.1.1.1: icmp_seq=2 ttl=253 time=4.081 ms
56 bytes from 100.1.1.1: icmp_seq=3 ttl=253 time=3.655 ms
56 bytes from 100.1.1.1: icmp_seq=4 ttl=253 time=3.828 ms--- Ping statistics for 100.1.1.1 ---
5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss
round-trip min/avg/max/std-dev = 3.378/3.918/4.650/0.432 ms
<PC-B>%Jul 14 22:00:39:090 2025 PC-B PING/6/PING_STATISTICS: Ping statistics for 100.1.1.1: 5 packet(s) transmitted, 5 packet(s) received, 0.0% packet loss, round-trip min/avg/max/std-dev = 3.378/3.918/4.650/0.432 ms.<PC-B>
<PC-B>ftp 100.1.1.1
Press CTRL+C to abort.
Connected to 100.1.1.1 (100.1.1.1).
220 FTP service ready.
User (100.1.1.1:(none)): stw
331 Password required for stw.
Password:
230 User logged in.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
不能 ping 通FTP-A但是可以 ping 通R1,说明PC-B的ftp需要在100.1.1.1上获取到



)










——图正则化算法)




的根与源)