文章目录
- 问题描述
- 解决过程
- 相关文章
问题描述
Android读prop值时,就算是system应用, 也需要selinux权限,否则会报错。
java代码如下
SystemProperties.get("ro.input.resampling", "")
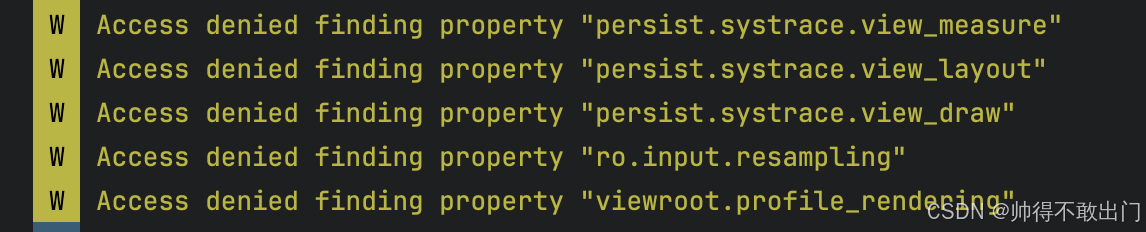
selinux报错如下
2025-06-28 17:57:25.971 6575-6575 com.xx W type=1400 audit(0.0:167): avc: denied { read } for name="u:object_r:default_prop:s0" dev="tmpfs" ino=22315 scontext=u:r:system_app:s0:c512,c768 tcontext=u:object_r:default_prop:s0 tclass=file permissive=0
解决过程
假设是test.te是system应用其对应test这个app的selinux的配置文件,test如果要读prop属性则需要在system_app.te中修改,不同的系统可能会不一样。
展锐
allow system_app vendor_default_prop:property_service { set };
mtk
allow system_app default_prop:file { read };
光改这里,编译固件是会报错:
neverallow check failed at out/target/product/uis7861_6h10_go_32b/obj/ETC/plat_pub_versioned.cil_intermediates/plat_pub_versioned.cil:9955(neverallow base_typeattr_219_31_0 default_prop_31_0 (file (ioctl read write create setattr lock relabelfrom append unlink link rename open watch watch_mount watch_sb watch_with_perm watch_reads)))<root>allow at out/target/product/uis7861_6h10_go_32b/obj/ETC/vendor_sepolicy.cil_intermediates/vendor_sepolicy.cil:5566(allow system_app default_prop_31_0 (file (read)))neverallow check failed at out/target/product/uis7861_6h10_go_32b/obj/ETC/plat_sepolicy.cil_intermediates/plat_sepolicy.cil:22867 from system/sepolicy/private/property.te:46(neverallow base_typeattr_222 base_typeattr_749 (file (ioctl read write create setattr lock relabelfrom append unlink link rename open watch watch_mount watch_sb watch_with_perm watch_reads)))<root>allow at out/target/product/uis7861_6h10_go_32b/obj/ETC/vendor_sepolicy.cil_intermediates/vendor_sepolicy.cil:5566(allow system_app default_prop_31_0 (file (read)))neverallow check failed at out/target/product/uis7861_6h10_go_32b/obj/ETC/plat_sepolicy.cil_intermediates/plat_sepolicy.cil:14268 from system/sepolicy/public/property.te:221(neverallow base_typeattr_222 default_prop (file (ioctl read write create setattr lock relabelfrom append unlink link rename open watch watch_mount watch_sb watch_with_perm watch_reads)))<root>allow at out/target/product/uis7861_6h10_go_32b/obj/ETC/vendor_sepolicy.cil_intermediates/vendor_sepolicy.cil:5566(allow system_app default_prop_31_0 (file (read)))
同时修改
system/sepolicy/private/property.te
system/sepolicy/prebuilts/api/31.0/private/property.te
搜索关键字“default_prop:property_service”
neverallow {domain-init-vendor_init
} default_prop:property_service set;
改成
neverallow {domain-init-vendor_init-system_app
} default_prop:property_service set;
搜索关键字“Neverallow coredomain to set vendor properties”
compatible_property_only(`# Neverallow coredomain to set vendor propertiesneverallow {coredomain-init-system_writes_vendor_properties_violators} {property_type-system_property_type-extended_core_property_type}:property_service set;
')
改成
compatible_property_only(`# Neverallow coredomain to set vendor propertiesneverallow {coredomain-init-system_writes_vendor_properties_violators-system_app} {property_type-system_property_type-extended_core_property_type}:property_service set;
')
只改这两处不够,否则会报错如下图:
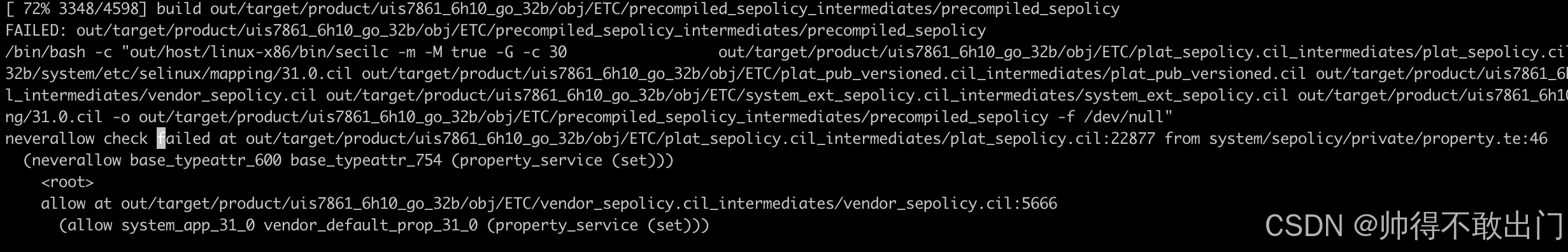
neverallow check failed at out/target/product/uis7861_6h10_go_32b/obj/ETC/plat_sepolicy.cil_intermediates/plat_sepolicy.cil:22877 from system/sepolicy/private/property.te:46(neverallow base_typeattr_600 base_typeattr_754 (property_service (set)))<root>allow at out/target/product/uis7861_6h10_go_32b/obj/ETC/vendor_sepolicy.cil_intermediates/vendor_sepolicy.cil:5666(allow system_app_31_0 vendor_default_prop_31_0 (property_service (set)))
根据错误提示定位到46行
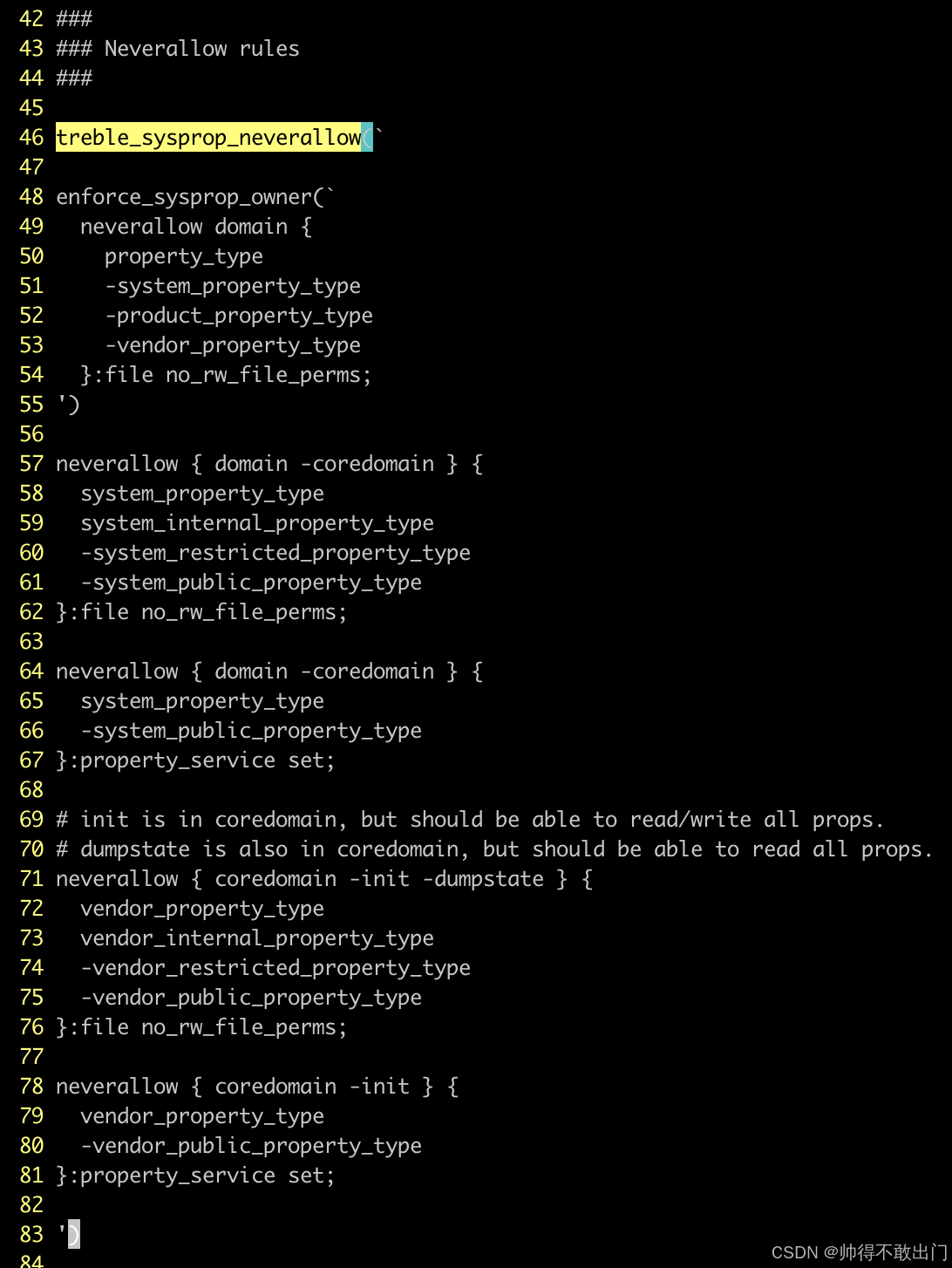
就是treble_sysprop_neverallow括号包含的内容导致冲突的。
treble_sysprop_neverallow(`enforce_sysprop_owner(`neverallow domain {property_type-system_property_type-product_property_type-vendor_property_type}:file no_rw_file_perms;
')neverallow { domain -coredomain } {system_property_typesystem_internal_property_type-system_restricted_property_type-system_public_property_type
}:file no_rw_file_perms;neverallow { domain -coredomain } {system_property_type-system_public_property_type
}:property_service set;# init is in coredomain, but should be able to read/write all props.
# dumpstate is also in coredomain, but should be able to read all props.
neverallow { coredomain -init -dumpstate } {vendor_property_typevendor_internal_property_type-vendor_restricted_property_type-vendor_public_property_type
}:file no_rw_file_perms;neverallow { coredomain -init } {vendor_property_type-vendor_public_property_type
}:property_service set;')
把-system_app加上,改成
treble_sysprop_neverallow(`enforce_sysprop_owner(`neverallow domain {property_type-system_property_type-product_property_type-vendor_property_type}:file no_rw_file_perms;
')neverallow { domain -coredomain -system_app } {system_property_typesystem_internal_property_type-system_restricted_property_type-system_public_property_type
}:file no_rw_file_perms;neverallow { domain -coredomain -system_app } {system_property_type-system_public_property_type
}:property_service set;# init is in coredomain, but should be able to read/write all props.
# dumpstate is also in coredomain, but should be able to read all props.
neverallow { coredomain -init -dumpstate } {vendor_property_typevendor_internal_property_type-vendor_restricted_property_type-vendor_public_property_type
}:file no_rw_file_perms;neverallow { coredomain -init -system_app } {vendor_property_type-vendor_public_property_type
}:property_service set;')
system/sepolicy/public/property.te
system/sepolicy/prebuilts/api/31.0/public/property.te
system_internal_prop(default_prop)
改成
system_public_prop(default_prop)
修改public/domain.te
同时修改
system/sepolicy/public/domain.te
system/sepolicy/prebuilts/api/31.0/public/domain.te
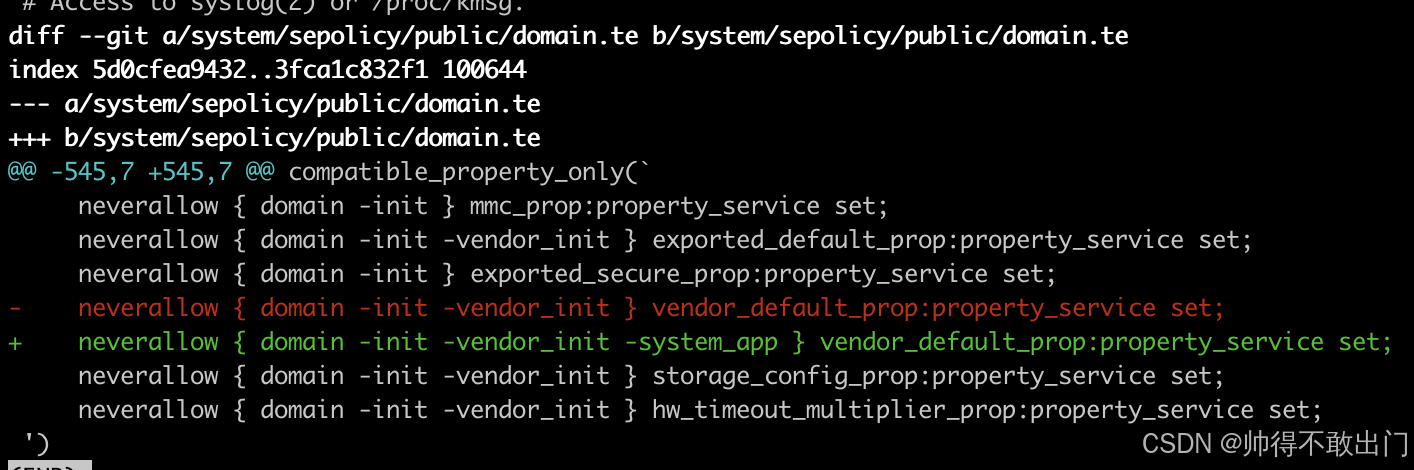
把
neverallow { domain -init -vendor_init } vendor_default_prop:property_service set;
改成
neverallow { domain -init -vendor_init -system_app } vendor_default_prop:property_service set;
如下图:
相关文章
MTK Android为某个APP单独添加selinux配置文件
MTK Android修改selinux允许system APP可读写sys与proc
Android获取selinux的setprop权限修改SystemProperties
Android13配置selinux让system应用可读sys,proc,SN号
作者:帅得不敢出门



)



)











